Changelog
Learn about what we shipped recently at DeepSource.
The AI Code Review Platform
Software development as we know it has undeniably, irrevocably changed. With AI coding agents writing almost all of our code, a static-only code review tool is no longer relevant. To serve our customers (and now their coding agents also) better, DeepSource is evolving.
In this changelog, we outline all that's new and changing in DeepSource for you. Here's everything that's new.
Introducing, AI Review
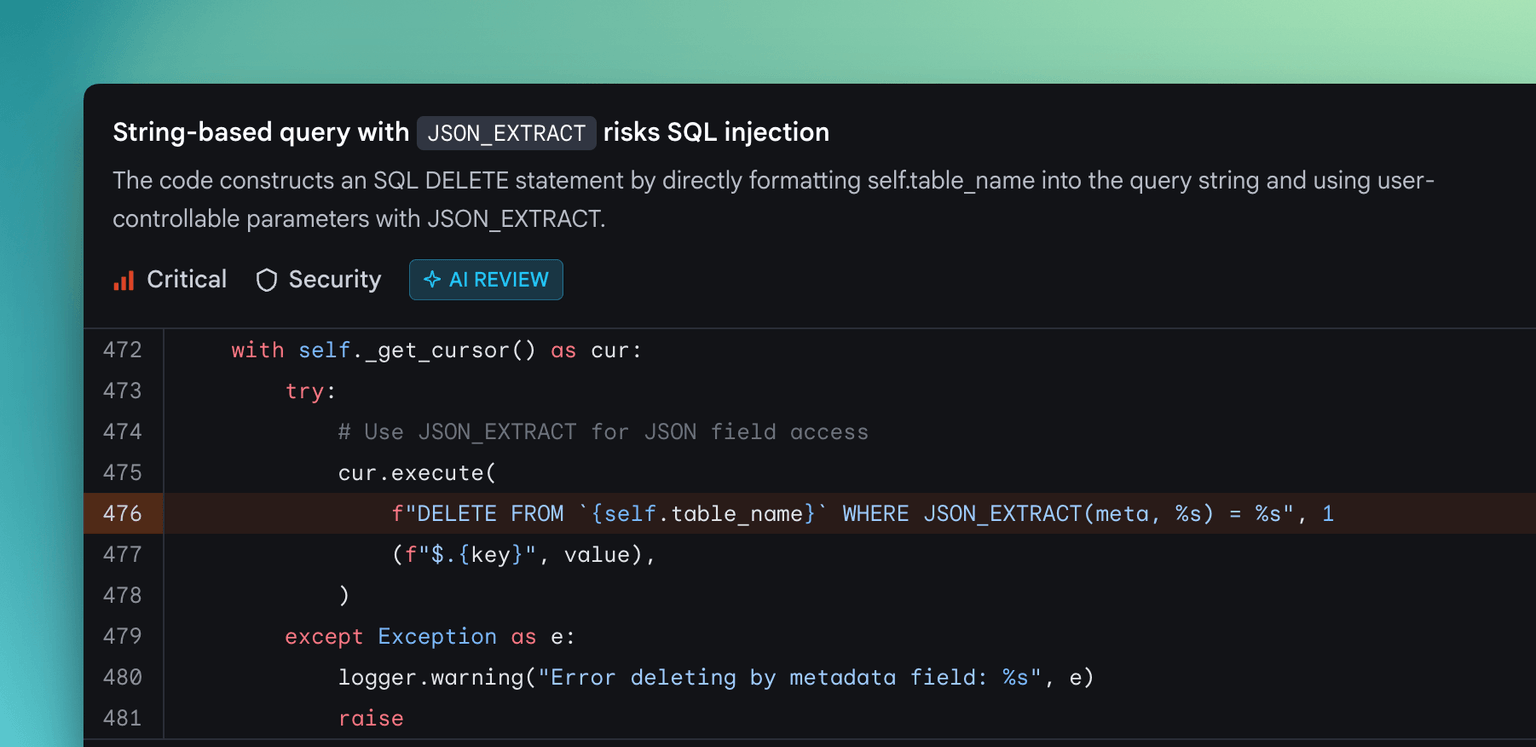
Our all-new AI code review engine now runs alongside static analysis on every pull request. As a result, DeepSource now detects novel code quality and security issues using AI that go beyond what our static analyzers could find on their own. The static analysis results are remarkably better now, with far fewer false positives (thanks to AI filtering) and better descriptions.
AI Review is enabled by default for all new customers. If you're an existing customer, you can enable it by switching on the "Enable AI Agents" flag in Policies → AI on your dashboard. You can review how the pay-as-you-go billing works for AI Review in the docs.
Inline review comments on pull requests

In addition to per-analyzer checks on your pull requests, DeepSource now posts inline review comments for issues detected directly on the diffs. Each issue comes with a detailed explanation of the code quality problem or security vulnerability found along with its severity, making it easier for developers to understand and take action on the feedback without leaving the SCM's interface.
Inline review comments are supported on GitHub, GitLab, Bitbucket (Cloud and Data Center), and Azure DevOps Services. It's enabled by default for all new customers. If you're an existing customer, you can toggle it in each repository's Settings → Quality Gates.
PR Report Card

Code review is not only about catching bugs. It's a feedback loop that helps the creator of the pull request improve their code. True for human developers, now true for AI coding agents.
Each pull request now gets a report card with structured, second-order feedback on the code across five dimensions — Security, Reliability, Complexity, Hygiene, and Coverage. All of these dimensions put together, provide a comprehensive view of the code quality and security of the pull request. The grade (A through D) gives a overview of how "good" the code is, and the detailed feedback gives the developer or the AI coding agent pointers on what they could do better.
Pricing plans and entitlement changes

With all these substantial changes to DeepSource's platform, we're also making some substantial changes to our pricing plans and entitlements to serve our customers more sustainably:
- We're deprecating the Free plan, and replacing it with the new Open Source plan, which gives open-source organizations free access to our static analysis capabilities. If you're currently on our Free plan, your account will be migrated to the Open Source plan on March 23, 2026. If you'd like to continue using DeepSource for your private repositories, we recommend upgrading to the Team plan.
- We're deprecating the Starter plan, and won't be offering it to new customers. If you're a current customer on the Starter plan, nothing is changing for you and you can continue being on this plan for as long as you want to. However, we won't be offering AI Review on this plan, and we recommend migrating to the new Team plan if you wish to use everything new that DeepSource has to offer.
- We're migrating the Business plan to the new Team plan. If you're a current customer on the Business plan, nothing is changing for you, and you can migrate to the new plan from your dashboard to get access to AI Review without any changes to your cost. As part of the new plan, you'll also get $120/seat/year (or $10/seat/month if billed monthly) bundled AI Review credits included in your subscription.
- There are no changes to our Enterprise Cloud and Enterprise Server plans. If you'd like to use AI Review, you can reach out to your point of contact and we'll get you onboarded.
- Going forward, DeepSource will review only those pull requests which are created by a member of the team on DeepSource. For all other pull requests, the review will be skipped and the developer can request to join the team using the link in the pull request's comment left by DeepSource. Once they're added to the team, the pull request will be automatically reviewed.
If you have any questions about any of the billing changes, please reach out to support and we're happy to assist.
Fixes and Improvements
- You can now export code review results of a PR from the detail page on DeepSource. Look for the Copy as Markdown button. This makes it easier for you to share findings with your AI coding assistants by copy-pasting and asking them to fix everything in a pull request.
- The team's home view is now simpler, and features a section for you to view all recent pull requests reviewed by DeepSource.
- Performance: We've made several improvements to the entire dashboard, and you should notice that the initial loading when opening the dashboard is much snappier, with several performance improvements across the dashboard.
- API: New types are now available in our GraphQL API for retrieving AI issues, OSS vulnerabilities, and PR report card.
If you've made it this far, thank you for reading this! This is one of the biggest product releases our team has pulled off and it took a good few months for us to make sure we transition all our customers smoothly. If you run into any issues, please reach out to support, or give us feedback on @deepsource.
SSO multi-IDP support
DeepSource now supports multiple teams sharing the same identity provider (IDP/Entity ID) for Single Sign-On. Users who have access to multiple IDPs will see a provider selection screen during login, making it easier to manage authentication across teams and organizations.
Fixes and Improvements
- Dashboard performance has been improved for teams with a large number of repositories.
- Fixed an issue with Bitbucket diff handling during merge conflicts.
Code formatters, team invitations, performance improvements
Transformers have been renamed to Code Formatters across the platform and the Public API. The new code_formatters type replaces the previous transformers type, which is now deprecated. All existing configurations will continue to work, but we recommend updating to use the new naming going forward.
Fixes and Improvements
- Free plan users can now view past invoices from the billing page.
- Fixed an issue where Bitbucket redirect URIs were not being handled correctly during OAuth authentication.
- Fixed race conditions that could occur when committing configuration changes to VCS.
- Dashboard load times have been improved across the board.
Agentic Secrets Detection
DeepSource's Secrets Analyzer now supports switching between two detection engines: Legacy (our existing static-only analysis engine), and the all new Hybrid AI Agent engine. This is now the recommended engine, and is powered by Narada, our open-source secrets classification model. To learn more, please read the announcement here.
You can switch the engine for your workspace in Settings -> General -> Preferences in your team dashboard. This is available to all teams on DeepSource Cloud. Refer to the docs here.

New in Analyzers
- Go: Added support for Go v1.25.3.
- Python: Maximum line-length checks now ignore common inline pragma markers and their trailing comments (for example:
# noqa,# pylint: disable=...,# skipcq,# type: ignore, and# pyright: ignore), so that these suppressions do not cause otherwise-valid lines to fail the rule. - Java: Reduced false positives for
JAVA-E1065by ignoring cases introduced by test-related Spring/Mockito annotations such as@SpyBean,@MockitoBean, and@MockitoSpyBean. - Kubelint: Reporting coverage has been expanded, so 9 new issue types are now detected.
Bun and uv are now supported in DeepSource SCA
DeepSource SCA now natively supports Bun and uv package managers.
For projects using Bun with JavaScript and uv with Python, click on Actions... -> Discover and sync all targets... in the Dependencies tab in the repository dashboard on DeepSource to trigger target discovery. Alternatively, you can also add the manifest files and lock files manually using the Add new target... button.
DeepSource Agents, Autofix AI, OIDC support
This release introduces DeepSource Agents for autonomous code analysis and remediation, along with Autofix AI powered by Large Language Models. We're also expanding our SCA integration with Vanta and adding OIDC support for GitHub Actions authentication.
DeepSource Agents
DeepSource Agents observe every line you or your AI write in your code base, reason about the changes with all available context of your code and your organization, and take action to secure your code — all on 100% autopilot.
For reasoning about your code, the agents access a comprehensive graph of your code and third-party dependencies, access long-term memory of facts about your organization, and take actions like creating pull requests, re-prioritizing CVEs, and suppressing false-positives. Read more at deepsource.com/agents.
The following agents are available today:
- Autofix™ Autopilot: Generates pull requests to resolve security issues detected during analysis.
- CVE Prioritization Agent: Looks at open-source vulnerabilities in your dependencies and adjusts the priority autonomously based on usage and exposure within your codebase.
- False Positive Triage Agent: Helps reduce noise by automatically identifying and suppressing likely false positives, cutting down manual review time.
Autofix™ AI
Five years ago, we introduced Autofix™ - an industry-first automated remediation engine that could fix issues in your code with a single click. We're excited to announce its evolution: Autofix™ AI, powered by Large Language Models.
While the legacy system handled about 30% of detected issues with deterministic fixes, Autofix AI leverages LLMs to generate context-aware, idiomatic fixes for nearly all issues identified by DeepSource. It analyzes not just the problematic code but also its surrounding context, including imports, related functions, and your project's coding patterns, to generate fixes.
For teams already using Autofix™, we've designed the transition to be frictionless. Simply visit your Team Settings page in DeepSource dashboard, navigate to the Autofix™ section, and select "Autofix™ AI" mode. Read more at deepsource.com/blog/autofix-ai.
Note: Autofix AI and DeepSource Agents are available to all existing users on DeepSource Cloud, with a generous free tier. We will soon announce paid plans and support for Enterprise Server, our on-premise offering.
SCA Integration with Vanta
DeepSource now fully integrates Software Composition Analysis (SCA) with Vanta, expanding beyond our previous support for SAST issues. Security and compliance teams can now automatically surface vulnerable open-source dependencies in their Vanta dashboard, giving them a unified view of code and dependency risks.
If you're an existing user of the Vanta integration, no action is required. Once SCA is enabled on a repository, it will be automatically reported to Vanta. More info at deepsource.com/blog/vanta-sca.
Support for OIDC
DeepSource now supports OpenID Connect (OIDC) authentication with GitHub Actions, eliminating the need to manage repository specific Data Source Names (DSNs) for test coverage reporting. This streamlines CI/CD workflows by leveraging GitHub's built-in OIDC provider for secure, short-lived token-based authentication.
Setting up OIDC is straightforward - simply configure your GitHub Actions workflow to use the OIDC provider and DeepSource will automatically authenticate your requests.
For detailed setup instructions, visit docs.deepsource.com/docs/guides/setup-test-coverage#with-github-actions-ci-using-oidc.
Fixes and Improvements
- Fixed an issue where the Export button was not working on the Public Reports page.
- Redesigned the Analysis Detail view under the History tab to highlight relevant information and improve focus on detected issues.
- The Dependencies tab now supports filtering vulnerabilities by CVSS and EPSS scores.
- You can now export the SBOM for a specific target in your repository in SPDX format, in addition to the existing CSV and JSON options.
- Vulnerability entries now display implied severity when modified by the CVE Prioritization Agent.
- Users can now regenerate an Autofix for a vulnerability after closing the previously generated pull request.
New in Analyzers
- Kotlin analyzer now supports versions 2.0 and 2.1
- Go analyzer adds support for version 1.24.1
- A rule to detect unused variables in C#